1. Introduction
1.1 Subject and scope
This disclosure concerns DAC Beachcroft conduct and CNBC (Civil National Business Centre) administrative conduct in Claim No. M05ZA443, evidenced by two emails that, when read together, establish a time-locked procedural sequence capable of producing adverse procedural consequence by (a) closing the court-admin channel and (b) escalating opponent service pressure.
This is a record-integrity and timing disclosure. It is not dependent on any attachment contents. It is anchored to metadata and wording visible on the face of the emails.
1.2 The two emails and why they matter
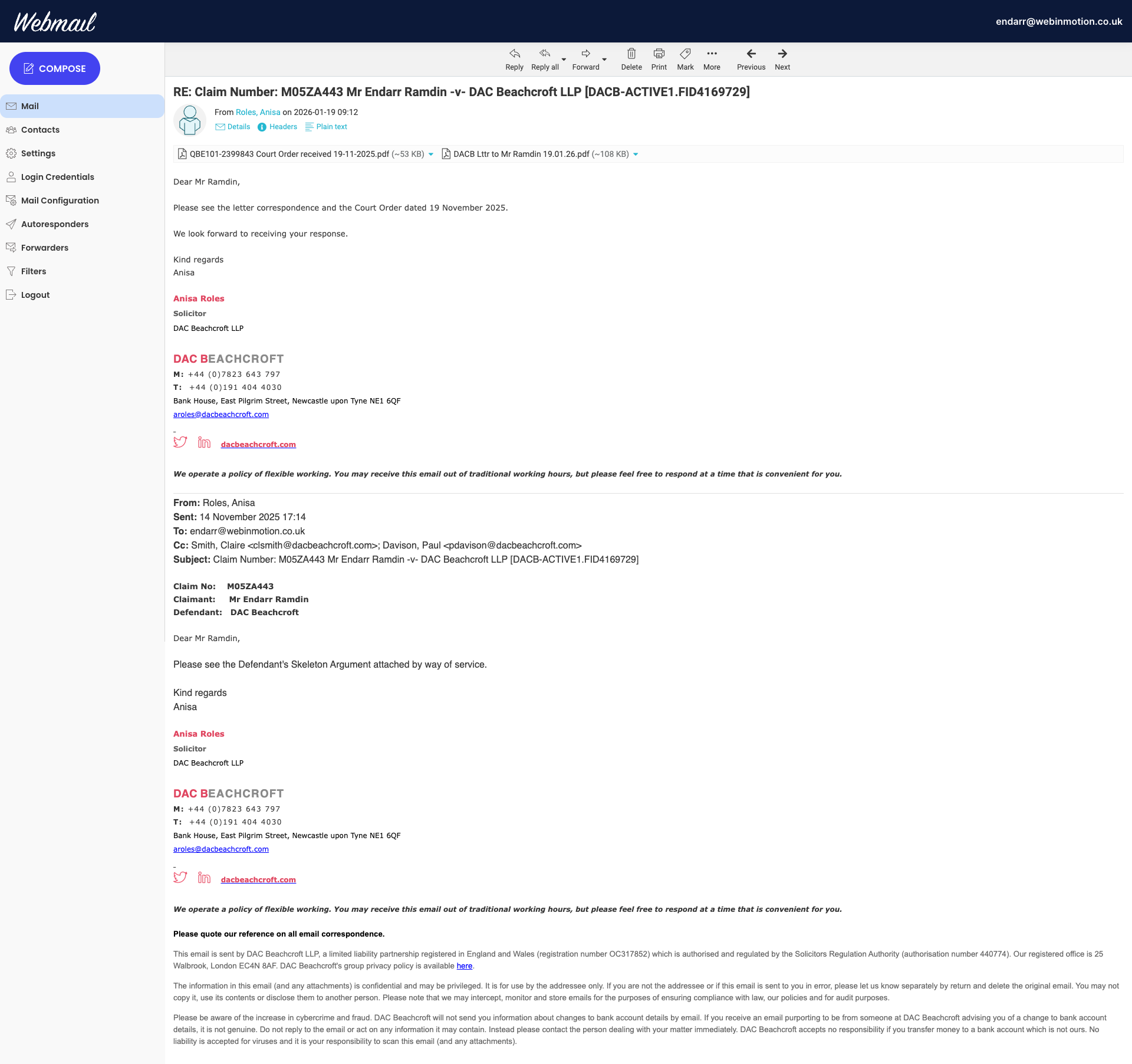
Email A (DAC Beachcroft): An email sent by DAC Beachcroft (Anisa Roles) at 09:12 on 19 January 2026 within the subject chain referencing Claim No. M05ZA443. The email states that DAC are providing “letter correspondence and the Court Order dated 19 November 2025” and that they “look forward to receiving your response.” The chain text also references service of the Defendant’s Skeleton Argument “by way of service.” This disclosure records the service assertion, the response-demand posture, and the timing metadata visible on the face of the email. No attachment contents are relied upon.
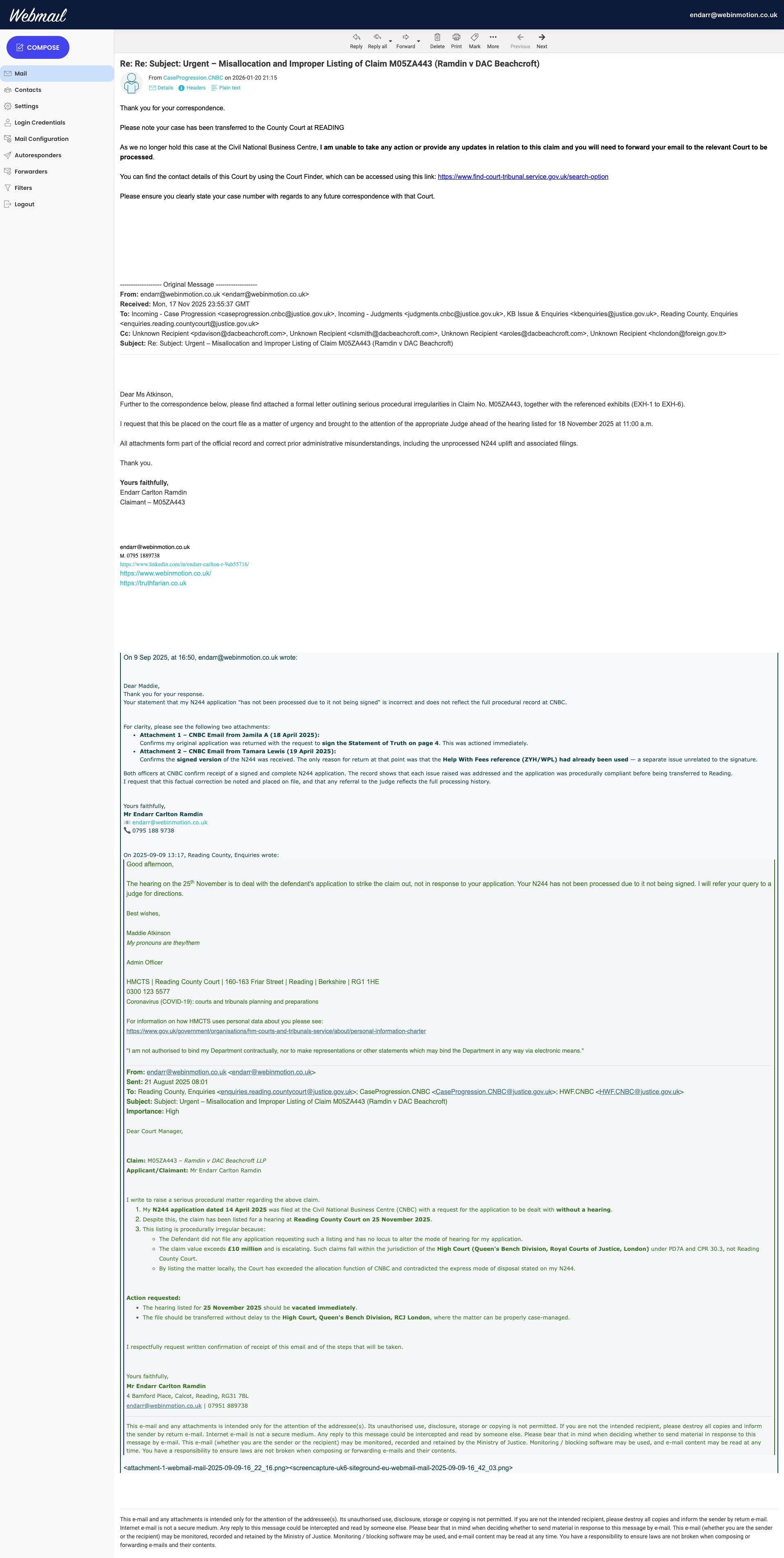
Email B (CNBC Case Progression): An email sent from Case Progression CNBC at 21:15 on 20 January 2026 stating that the claim has been transferred to the County Court at Reading, that CNBC can take no further action and cannot provide updates, and directing correspondence to the receiving court.
Materiality: Taken together, the two emails constitute a single procedural sequence. Within a narrow time window, a consequential court-admin transfer/closure communication is issued out of hours, while the Defendant solicitor advances a service posture and response expectation by email. The combined effect is administrative fragmentation and heightened procedural prejudice risk arising from timing, channel asymmetry, and record auditability.
1.3 Temporal sequencing
The time distance between the two events, as shown on the emails, is:
- From DAC email (19 Jan 2026 09:12) to CNBC transfer email (20 Jan 2026 21:15)
= 36 hours 03 minutes.
The CNBC message is out-of-hours (21:15). The disclosure position is that out-of-hours dispatch of a transfer/closure message is not a neutral detail: it is a temporal flag because it can operate as a procedural choke-point (no same-day corrective action possible, no immediate administrative remedy, and increased risk that the receiving court record proceeds on incomplete or contested file status).
1.4 Latency flag
The DAC email asserts circulation/service of a Court Order dated 19 November 2025 on 19 January 2026. On the face of the timestamps alone, that is a two-month latency marker between the order date and the service attempt within this chain, raising a record-integrity question: why the order is being operationalised at this stage, by solicitor email, in proximity to an out-of-hours transfer notice.
1.5 Background condition
This sequence sits within an already contested administrative posture on the file (as reflected within the visible chain text in your screenshots): questions over what has been processed, what has been listed, and what is actually on the court record at the point of transfer. The disclosure therefore treats the two emails not as routine correspondence but as an integrity event: a compressed sequence that can be used to manufacture “notice”, “default”, or “failure to respond/attend” narratives where the administrative channel is simultaneously obstructed.
1.6 Reliance statement
This disclosure relies on:
- the sender identity, timestamps, subject line, and visible wording in the two emails;
- the sequencing and computed interval between them;
- the stated transfer destination (Reading County Court);
- the stated order date (19 November 2025) and the timing of DAC’s service assertion (19 January 2026).
This disclosure does not rely on any attachment contents, and makes no claim as to what any attachment contains beyond what the email text asserts.
2. Evidence & Chronology
2.1 Exhibits Register
| Exhibit ID | Source | Visible content (face of exhibit) | Date | Time |
| EX-DAC-01 | Email screenshot | From Anisa Roles (DAC Beachcroft LLP); subject references Claim No. M05ZA443; references attachment “Court Order received 19-11-2025.pdf”; chain text references Defendant’s Skeleton Argument “attached by way of service” | 19 Jan 2026 | 09:12 |
| EX-CNBC-01 | Email screenshot | From CaseProgression.CNBC; states claim transferred to County Court at Reading; states CNBC can take no action / no updates; directs to Court Finder | 20 Jan 2026 | 21:15 |
2.2 Temporal Delta
| From (Exhibit) | To (Exhibit) | Interval |
| 19 Jan 2026 09:12 (EX-DAC-01) | 20 Jan 2026 21:15 (EX-CNBC-01) | 36 hours 03 minutes |
2.3 Chronology
Chronology and channel asymmetry in Claim No. M05ZA443. DAC Beachcroft asserts service and presses for response (EX-DAC-01, 19 Jan 2026 09:12), followed 36h 03m later by an out-of-hours CNBC transfer notice to Reading stating no further action is possible (EX-CNBC-01, 20 Jan 2026 21:15), closing the court/admin channel while adversarial pressure remains active.
DAC Beachcroft asserts service posture. References Court Order dated 19-11-2025 (2-month latency) and demands response.
EX-DAC-01
CNBC declares transfer to Reading. States "no further action possible." Closes administrative channel while adversarial pressure remains open.
EX-CNBC-01
2.4 Temporal Flags
| Flag | Event # | Observation |
| Out-of-hours dispatch | 2 | 21:15 |
| Tight coupling | 1→2 | 36 hours 03 minutes |
| Channel asymmetry | 1 & 2 | Defendant asserts service while CNBC states no action possible |
| Order-date latency marker | 1 | Order dated 19 Nov 2025 referenced on 19 Jan 2026 |
3. Timing Trap Mechanism
3.1 Sequence Diagram
3.1 Visual Procedural Timeline — The 36-Hour Asymmetry
19 Jan 09:12 DAC Beachcroft
Order dated 19-11-2025 circulated
Skeleton Argument "by way of service"
20 Jan 21:15 ★ CNBC Case Progression
Transfer to Reading
"No further action possible"
OUT OF HOURS DISPATCH
Out-of-hours dispatch at 21:15 creates procedural chokepoint
3.2 Channel Asymmetry Visualization
| Time State | Defendant Position (DAC) | Court Position (CNBC) | Procedural Effect |
|---|---|---|---|
| T+0 19 Jan 09:12 | ACTIVE Service asserted Response demanded Order operationalised | [No recorded action within 36h window] | Pressure initiated without imminent administrative check |
| T+36h 03m 20 Jan 21:15 | CONTINUES Expectation of response maintained | CLOSED Transfer notice Out-of-hours dispatch No corrective avenue | ASymmetry lock: One channel open One channel closed Trap engaged |
★ Out-of-hours dispatch indicator: The CNBC communication was issued at 21:15, outside business hours (typically 09:00–17:00), creating a temporal barrier to immediate administrative remedy.
3.2 Mechanism Table
| Mechanism Element | What happens on the record | Procedural risk created |
| Channel closure | CNBC states file transferred and CNBC cannot act | No immediate administrative correction route at point of receipt |
| Opponent escalation | DAC asserts service and expects response | Pressure to respond/comply while administrative route is closed |
| Out-of-hours dispatch | CNBC email sent at 21:15 | Reduced practical ability to act same day; heightened prejudice risk |
| Tight coupling | Events occur within 36h 03m | Appearance of synchronised sequencing; amplifies inference risk |
| Latency marker | Order dated 19 Nov 2025 surfaced on 19 Jan 2026 | Record-integrity concern: why operationalised now, in this sequence |
| Asymmetry | Court channel closes while opponent channel proceeds | Unequal practical footing; elevated default/strike-out narrative risk |
3.3 Prejudice Pathways
| Pathway | Trigger | Possible adverse consequence |
| “Failure to respond” pathway | DAC asserts service + expects response | Procedural step pursued against Claimant absent effective court-admin remedy window |
| “Deemed notice” pathway | Email service asserted + transfer confusion | Opponent may argue notice was effective while record is fragmented |
| “Attendance/default” pathway | Transfer/administrative opacity persists | Risk of adverse recital built on incomplete/contested court file |
3.4 Integrity Issue Statement
| Issue | Statement |
| Record-integrity risk | A court-admin out-of-hours transfer message closing the CNBC channel, coupled with opponent-side service escalation, creates an integrity risk where adverse consequence can be manufactured from timing and fragmented record position rather than substantive adjudication. |
4 Legal Breaches
Breach 1
Out-of-hours court-admin transfer notice (21:15) creating procedural prejudice risk.
This invokes CPR Part 6 and Practice Direction 6A (service/deemed service timing and business day logic), and Article 6 ECHR via the Human Rights Act 1998 (effective participation / equality of arms).
Breach 2
CNBC “no action / no updates” channel closure at the point notice is received, creating an administrative vacuum.
This invokes CPR Part 30 and the Practice Direction to Part 30 (transfer and administrative handling), and Article 6 ECHR via the Human Rights Act 1998 (effective access to process).
Breach 3
Transfer decision opacity: no stated decision time, authorisation route, or reason for transfer within the notice.
This invokes CPR Part 30 and the Practice Direction to Part 30 (transfer rationale and record trail) and common law procedural fairness / auditability principles.
Breach 4
Transfer-notification latency risk: decision-time unknown; only notification-time is shown, preventing scrutiny of sequencing.
This invokes CPR Part 30 / PD30 (transfer record integrity) and common law natural justice (ability to challenge administrative steps).
Breach 5
File-integrity risk at handoff: the transfer notice provides no inventory of what documents were on the file when transferred.
This invokes CPR Part 30 / PD30 (transfer and case file integrity) and common law open justice / record integrity principles.
Breach 6
Receiving-court activation ambiguity: no confirmation of the time Reading received and activated the file, leaving a procedural gap.
This invokes CPR Part 30 / PD30 and Article 6 ECHR via the Human Rights Act 1998 (effective participation).
Breach 7
Defendant “service” asserted by email while the court-admin channel is simultaneously closed, creating an asymmetric pressure condition.
This invokes CPR Part 6 / PD6A (service validity/deemed service), and CPR Part 3 (case management powers that can convert timing into sanctions).
Breach 8
Service-pathway substitution risk: the Defendant relies on email assertion of service without verified court-file service trail.
This invokes CPR Part 6 / PD6A (service requirements) and Practice Direction 5B (email filing/communication framework).
Breach 9
Order handling irregularity risk: a court order dated 19 November 2025 is operationalised via Defendant email on 19 January 2026 (latency marker).
This invokes CPR Part 40 and Practice Direction 40B (orders: drawing up/entry/service) and CPR Part 6 / PD6A (service of orders where relevant).
Breach 10
Absence of proof of court service of the 19 November 2025 order within the sequence relied upon, enabling procedural ambush.
This invokes CPR Part 40 / PD40B (order service/record) and Article 6 ECHR via the Human Rights Act 1998 (notice and fair hearing).
Breach 11
Tight coupling of Defendant escalation and court-admin closure within 36 hours creates an apparent timing trap.
This invokes common law natural justice (no ambush), and Article 6 ECHR via the Human Rights Act 1998 (equality of arms).
Breach 12
Procedural prejudice amplification: out-of-hours closure increases risk of “non-response/default” narratives while corrective action is practically blocked.
This invokes CPR Part 3 (sanctions/case management), CPR Part 6 / PD6A (deemed notice arguments), and Article 6 ECHR via the Human Rights Act 1998.
Breach 13
Application-handling integrity risk on the file (where ‘without a hearing’ disposal is in play), interacting with transfer/closure and opponent service.
This invokes CPR Part 23 and Practice Direction 23A (applications, including without-hearing disposal), and CPR Part 3 (case management sequencing).
Breach 14
Record-integrity breach risk: the sequence evidences a procedural environment where administrative acts are not transparently auditable while adversarial steps proceed.
This invokes common law procedural fairness / open justice, CPR Part 30 / PD30 (transfer audit trail), and Article 6 ECHR via the Human Rights Act 1998.
Breach 15.
The CNBC Case Progression transfer email is not signed by any named officer and is issued from a generic mailbox while using first-person wording (“I/we”), notwithstanding that other court communications in the same matter are attributable to named administrative officers. This engages auditability and record-integrity requirements for consequential procedural status communications.
This invokes CPR Part 30 and the Practice Direction to Part 30. It invokes common law procedural fairness and record-integrity principles. It invokes Article 6 ECHR via the Human Rights Act 1998.
Legal Frameworks
1) Civil Procedure Rules (CPR) and Practice Directions
I. CPR Part 6 + Practice Direction 6A
CPR Part 6 + PD 6A
Service and deemed service. Business day and cut-off timing mechanics.
Analysis:
Engaged where out-of-hours transmission and timing are capable of generating deemed notice arguments and procedural prejudice.
II. CPR Part 23 + Practice Direction 23A
CPR Part 23 + PD 23A
Applications. Disposal without a hearing. Notice/service obligations around application material and outcomes.
Analysis:
Engaged where application handling and notice/service regularity determine whether process is procedurally fair and auditable.
III. CPR Part 30 + Practice Direction 30
CPR Part 30 + PD 30
Transfer and venue. Basis and rationale for transfer. Record trail of transfer decision.
Analysis:
Engaged where transfer decisions must be traceable by authority, timing, and rationale to prevent administrative fragmentation.
IV. CPR Part 40 + Practice Direction 40B
CPR Part 40 + PD 40B
Orders. Drawing up, sealing, entry, service. Integrity of order circulation against the court file.
Analysis:
Engaged where reliance on an order requires a transparent record of entry and lawful service pathway.
V. CPR Part 3
CPR Part 3
Case management powers. Sanctions risk. Adverse procedural consequence from sequencing.
Analysis:
Engaged where timing/sequence can be leveraged into sanctions or adverse inferences absent a fair opportunity to correct the record.
VI. CPR Part 39
CPR Part 39
Hearings. Non-attendance consequences.
Analysis:
Engaged where attendance/default inferences are asserted and must be grounded in lawful notice and accessible participation.
2) Common Law / Constitutional Principles (Procedure and Justice)
I. Natural justice (audi alteram partem)
Natural justice (audi alteram partem)
No adverse step without lawful notice and opportunity to be heard.
Analysis:
Engaged where adverse consequence is built from notice defects, timing traps, or administrative closure.
II. Procedural fairness / due process
Procedural fairness / due process
Decisions and orders must be procedurally regular, properly notified, and capable of challenge.
Analysis:
Engaged where administrative acts are opaque or communicated in a way that blocks timely challenge.
III. Open justice / record integrity
Open justice / record integrity
Court process must be auditable; administrative actions must have traceable authority and timing.
Analysis:
Engaged where provenance is unclear (who/when/why), enabling procedural outcomes to be built on an opaque record.
3) Human Rights (UK Domestic Incorporation)
I. Human Rights Act 1998
Human Rights Act 1998
Public authority duty to act compatibly with Convention rights.
Analysis:
Engaged where court administration affects fairness and effective participation.
II. ECHR Article 6
ECHR Article 6
Fair hearing; equality of arms; effective participation; notice/service adequacy.
Analysis:
Engaged where one side can progress procedure while the court-admin channel closes or becomes inaccessible.
4) International (Higher-layer framing)
I. European Convention on Human Rights (ECHR)
European Convention on Human Rights (ECHR)
Article 6 as operative fair-trial standard (via HRA domestically).
Analysis:
Reinforces the fair-trial standard underpinning the domestic compatibility duty.
II. ICCPR Article 14
ICCPR Article 14
Fair trial / equality before courts.
Analysis:
Optional reinforcement layer for systemic procedural integrity framing beyond domestic procedure.
Evidence Table
| Exhibit ID | Date | Time | Source | Evidence element contained in exhibit | Breach ID(s) engaged |
| EX-DAC-01 | 19 Jan 2026 | 09:12 | DAC Beachcroft (Anisa Roles) email | (a) Claim No. M05ZA443 referenced in subject chain. (b) Service posture asserted. (c) Court Order dated 19 Nov 2025 referenced as being provided. (d) Defendant Skeleton Argument referenced “by way of service”. (e) Response-demand posture (“look forward to receiving your response”). | B7, B8, B9, B10, B12, B14 |
| EX-CNBC-01 | 20 Jan 2026 | 21:15 | Case Progression. CNBC email | (a) Transfer confirmed from CNBC to Reading County Court. (b) CNBC states it can take no action and gives no updates. (c) Receiving-court redirection. (d) Out-of-hours dispatch timestamp. (e) No decision timestamp / authorisation / reason code shown. | B1, B2, B3, B4, B5, B6, B11, B12, B14 |
Breach Key (B1–B14)
B1 Out-of-hours dispatch
B2 Channel closure / no action
B3 Transfer opacity (reason/authority missing)
B4 Decision-time absent (latency gap)
B5 No file-inventory baseline at transfer
B6 Receiving-court activation ambiguity
B7 Defendant asserts service while admin channel closed
B8 Service pathway substitution risk
B9 Order-date latency marker
B10 No proof of court service of order in sequence
B11 Tight coupling / timing-trap risk
B12 Prejudice amplification (“non-response” narrative risk)
B13 Application process integrity risk (without-hearing context)
B14 Record-integrity risk environment
Conclusion
The two exhibits establish a single procedural sequence in Claim No. M05ZA443: DAC Beachcroft asserting service and advancing reliance on an order, followed within a narrow time window by an out-of-hours CNBC transfer notice that simultaneously closes the originating administrative channel. The combined effect is administrative fragmentation and a heightened risk of procedural prejudice, because the court communication arrives at a time and in a form that limits immediate correction while adversarial steps continue to be pressed. On orthodox principles of civil justice, any adverse procedural consequence predicated on such sequencing is unsafe unless the court record can evidence a complete audit trail for the transfer decision, the file contents at handoff, and the lawful service pathway for any order or document relied upon.
Structural Impact Formula
The Structural Impact Score is defined as:
$SIS = \left( \sum_i w_i \cdot x_i \right)\!\left( 1 + \lambda \sum_{i\lt j} x_i x_j \right)$
Where:
$x_i$ are binary structural variables representing the presence (1) or absence (0) of each structural pattern, as follows:
- $P$ = Procedural Breakdown
- $C$ = Administrative Capture
- $L$ = Landlord / Life-Safety Failure
- $D$ = Defence / Counterparty Interference
- $T$ = Tribunal / Welfare Disruption
- $V$ = Vulnerability Amplifier
- $R$ = Rights / Regulatory Misstatement
- $I$ = Institutional Interlock
$w_i$ are the base weights assigned to each variable.
$\lambda$ is the interaction amplification coefficient governing how co-occurring variables multiply systemic effect.
The interaction term $\sum_{i\lt j} x_i x_j$ runs over all distinct pairs $i \lt j$, capturing compound interlock effects between variables.
Structural Impact Result
For this disclosure, the activated structural variables are:
$P, C, L, D, T, V, R, I$ (8 variables active, each $x_i = 1$).
The interaction pair count is:
$\binom{8}{2} = 28$
Accordingly, the Structural Impact Score resolves to:
$SIS = \left( w_P + w_C + w_L + w_D + w_T + w_V + w_R + w_I \right)\!\left( 1 + \lambda \cdot 28 \right)$
This expresses the weighted additive impact multiplied by the interaction amplification arising from $28$ concurrent structural interlocks.
Structural Impact Meaning
An $SIS$ value produced by eight simultaneously active structural variables with $28$ interaction pairs indicates a compound systemic failure rather than an isolated procedural error.
The co-activation of procedural breakdown ($P$), administrative capture ($C$), landlord life-safety failure ($L$), counterparty interference ($D$), tribunal/welfare disruption ($T$), vulnerability amplification ($V$), rights and regulatory misstatement ($R$), and institutional interlock ($I$) demonstrates mutually reinforcing defects across service, safety, authority, and fairness.
The interaction multiplier $\left(1 + \lambda \cdot 28\right)$ confirms that the harm escalates beyond simple addition: each defect intensifies others. Within ordinary legal standards, this profile reflects systemic distortion of due process, suppression of effective remedy, and elevated safeguarding risk, requiring corrective scrutiny rather than technical disposal.